网络安全之IPSEC路由基本配置
目录
网络安全之IPSEC路由基本配置
IPSEC配置的前提分析
协议分析
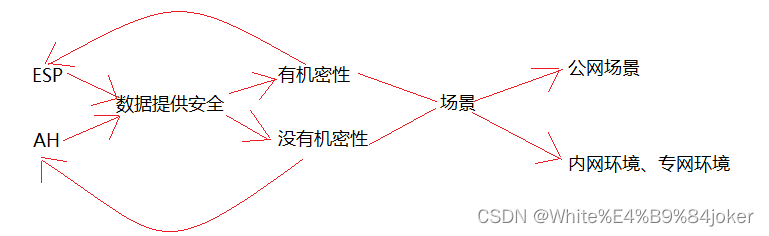
传输模式分析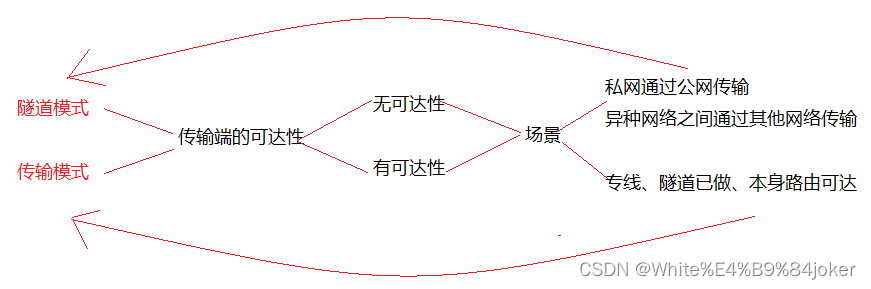
IPSEC路由中的配置
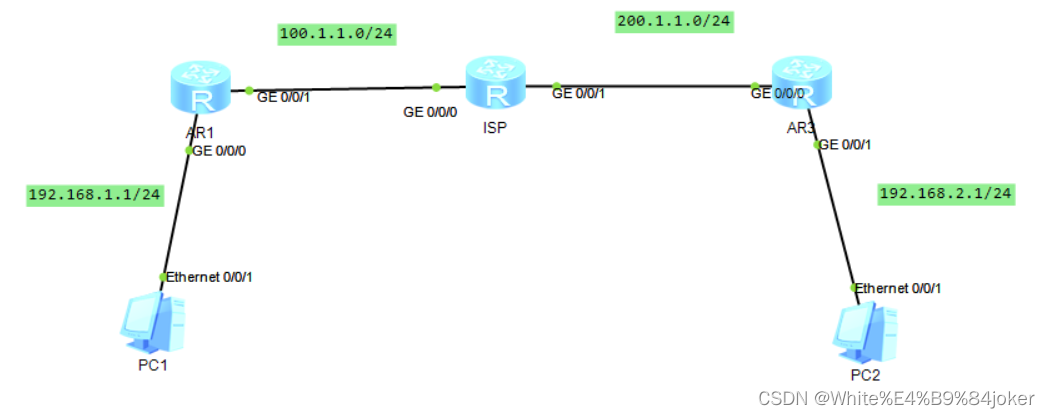
图谱图
注意:
此场景为私网之间配置
配置公网可达
R1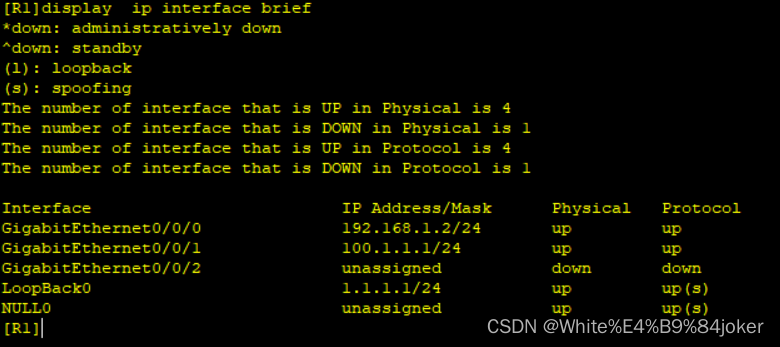
ISP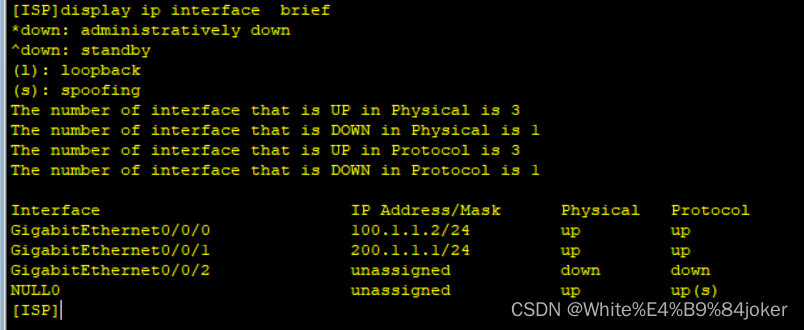
R3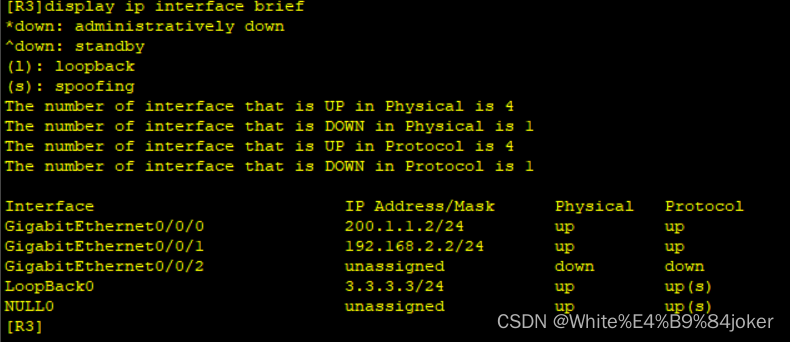
配置静态路由使得公网可达
[R1]ip route-static 192.168.2.0 24 100.1.1.2
[R1]ip route-static 200.1.1.0 24 100.1.1.2
[R3]ip route-static 100.1.1.0 24 200.1.1.1
[R3]ip route-static 192.168.1.0 24 200.1.1.1R1配置IKE SA的安全提议
[R1]ike proposal 1 --- 选择安全提议编号
[R1-ike-proposal-1]encryption-algorithm ?
3des-cbc 168 bits 3DES-CBC
aes-cbc-128 Use AES-128
aes-cbc-192 Use AES-192
aes-cbc-256 Use AES-256
des-cbc 56 bits DES-CBC --- 比较弱,一般不选
[R1-ike-proposal-1]encryption-algorithm 3des-cbc
[R1-ike-proposal-1]authentication-algorithm ? --- 认证加密算法
aes-xcbc-mac-96 Select aes-xcbc-mac-96 as the hash algorithm
md5 Select MD5 as the hash algorithm
sha1 Select SHA as the hash algorithm
sm3 Select sm3 as the hash algorithm
[R1-ike-proposal-1]authentication-algorithm sha1 --- 选择哈希算法
[R1-ike-proposal-1]authentication-method ? --- 认证模式
digital-envelope Select digital envelope key as the authentication method
pre-share Select pre-shared key as the authentication method
rsa-signature Select rsa-signature key as the authentication method
[R1-ike-proposal-1]authentication-method pre-share --- 域共享
[R1-ike-proposal-1]dh ? --- 选择DH算法
group1 768 bits Diffie-Hellman group
group14 2048 bits Diffie-Hellman group
group2 1024 bits Diffie-Hellman group
group5 1536 bits Diffie-Hellman group
[R1-ike-proposal-1]dh group5 --- 一般选2以上强度,1太低
[R1-ike-proposal-1]sa duration ? --- 安全联盟周期
INTEGER<60-604800> Value of time(in seconds), default is 86400
[R1-ike-proposal-1]sa duration 3600
R1配置 IKE SA 的身份认证信息
[R1]ike peer 1 ? --- 选择ike版本
v1 Only V1 SA's can be created
v2 Only V2 SA's can be created
<cr> Please press ENTER to execute command
[R1]ike peer 1 v1
[R1-ike-peer-1]exchange-mode ? --- 选择模式
aggressive Aggressive mode --- 野蛮
main Main mode --- 主模式
[R1-ike-peer-1]exchange-mode main --- 主模式
[R1-ike-peer-1]pre-shared-key ? --- 预共享密钥
cipher Pre-shared-key with cipher text --- 本地不加密
simple Pre-shared-key with plain text --- 本地加密
[R1-ike-peer-1]pre-shared-key cipher 123
[R1-ike-peer-1]ike-proposal 1 --- 调用安全提议编号
[R1-ike-peer-1]remote-address 200.1.1.2 --- 对方IP
野蛮模式配置
ike peer yyy v1 exchange-mode aggressive //设置为野蛮模式 pre-shared-key simple 999 ike-proposal 1 local-id-type name //定义本地ID为name remote-name kkk //远程ID是 kkk remote-address 200.1.1.1
R3配置IKE SA的安全提议
[R3]ike proposal 1
[R3-ike-proposal-1]encryption-algorithm 3des-cbc
[R3-ike-proposal-1]dh group5
[R3-ike-proposal-1]authentication-algorithm sha1
[R3-ike-proposal-1]sa duration 3600
[R3-ike-proposal-1]qR3配置 IKE SA 的身份认证信息
[R3]ike peer 1 v1
[R3-ike-peer-1]exchange-mode main
[R3-ike-peer-1]pre-shared-key cipher 123
[R3-ike-peer-1]ike-proposal 1
[R3-ike-peer-1]remote-address 100.1.1.1
[R3-ike-peer-1]R1配置IPSEC的安全提议
[R1]ipsec proposal 1 --- 选择安全协议号
[R1-ipsec-proposal-1]
[R1-ipsec-proposal-1]transform ? --- 选择封装协议
ah AH protocol defined in RFC2402
ah-esp ESP protocol first, then AH protocol
esp ESP protocol defined in RFC2406
[R1-ipsec-proposal-1]transform esp --- 选择ESP协议
[R1-ipsec-proposal-1]esp authentication-algorithm ? --- 选择认证算法
md5 Use HMAC-MD5-96 algorithm
sha1 Use HMAC-SHA1-96 algorithm
sha2-256 Use SHA2-256 algorithm
sha2-384 Use SHA2-384 algorithm
sha2-512 Use SHA2-512 algorithm
sm3 Use SM3 algorithm
[R1-ipsec-proposal-1]esp authentication-algorithm sha2-512
[R1-ipsec-proposal-1]esp encryption-algorithm ? --- 加密算法
3des Use 3DES
aes-128 Use AES-128
aes-192 Use AES-192
aes-256 Use AES-256
des Use DES
sm1 Use SM1
<cr> Please press ENTER to execute command
[R1-ipsec-proposal-1]esp encryption-algorithm aes-128
[R1-ipsec-proposal-1]encapsulation-mode tunnel --- 选择隧道模式
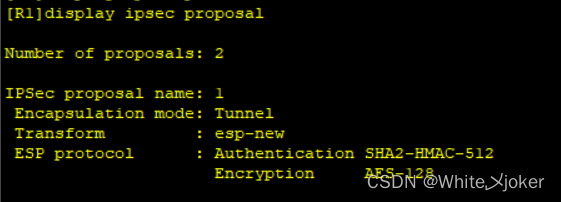
[R1]display ipsec proposal --- 查询配置的IPSEC
R1配置感兴趣流
[R1]acl 3000
[R1-acl-adv-3000]rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.1
68.2.0 0.0.0.255
R1配置安全策略集
[R1]ipsec policy k 1 ? --- 选择协议
isakmp Indicates use IKE to establish the IPSec SA
manual Indicates use manual to establish the IPSec SA
<cr> Please press ENTER to execute command
[R1]ipsec policy k 1 isakmp --- 定义安全策略编号与协议
[R1-ipsec-policy-isakmp-k-1]proposal 1 --- 调用IPSEC SA 提议
[R1-ipsec-policy-isakmp-k-1]ike-peer 1 --- 调用身份认证信息
[R1-ipsec-policy-isakmp-k-1]security acl 3000 --- 调用感兴趣流R3配置IPSEC的安全提议
[R3]ipsec proposal 1
[R3-ipsec-proposal-1]transform esp
[R3-ipsec-proposal-1]esp authentication-algorithm sha2-512
[R3-ipsec-proposal-1]esp encryption-algorithm aes-128
[R3-ipsec-proposal-1]encapsulation-mode tunnel
R3配置感兴趣流
[R3]acl 3000
[R3-acl-adv-3000]rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 192.1
68.1.0 0.0.0.255R3配置安全策略集
[R3]ipsec policy k 1 isakmp
[R3-ipsec-policy-isakmp-k-1]proposal 1
[R3-ipsec-policy-isakmp-k-1]ike-peer 1
[R3-ipsec-policy-isakmp-k-1]security acl 3000
在接口调安全策略集
[R1-GigabitEthernet0/0/1]ipsec policy k
[R3-GigabitEthernet0/0/0]ipsec policy k启动
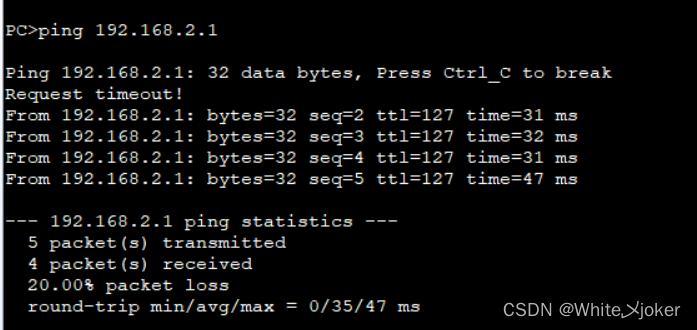
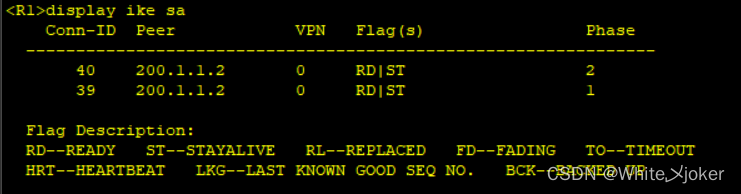
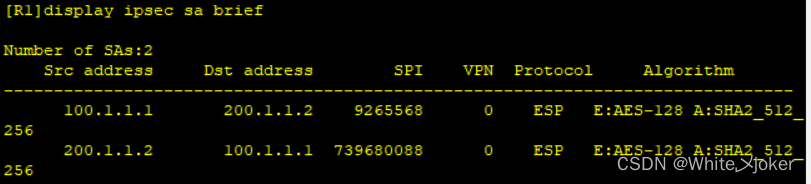
测试